Understanding Networked Storage: The Role of Drive Letters
Related Articles: Understanding Networked Storage: The Role of Drive Letters
Introduction
With enthusiasm, let’s navigate through the intriguing topic related to Understanding Networked Storage: The Role of Drive Letters. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
Understanding Networked Storage: The Role of Drive Letters
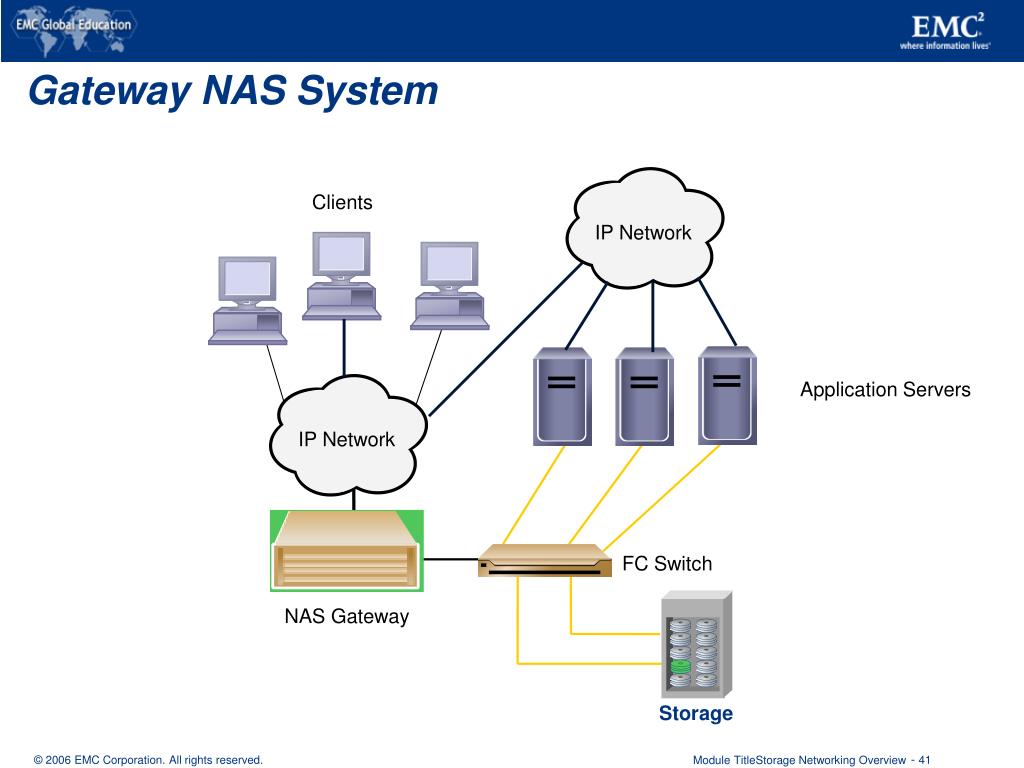
In the realm of computer networks, drive letters serve as convenient labels for accessing various storage locations. These locations can be local hard drives within a single computer, or they can be remote storage devices accessible across a network. The "J drive," like other drive letters, represents a specific storage location within a network environment.
The Importance of Networked Storage
Networked storage, often referred to as "shared storage," offers numerous benefits:
- Centralized Data Management: Networked storage allows for the consolidation of data in a single location, making it easier to manage, back up, and share information across an organization.
- Enhanced Collaboration: Users can access and share files simultaneously, fostering collaboration and improving workflow efficiency.
- Scalability and Flexibility: Networked storage systems can be easily scaled to accommodate growing data storage needs, providing flexibility in adapting to changing requirements.
- Improved Data Security: Networked storage solutions typically offer robust security features, including access controls, encryption, and disaster recovery options.
Accessing Networked Storage: The "J Drive" Example
The "J drive" is a common designation for a shared storage location within a network. Accessing this drive usually involves a combination of network settings and user authentication. Here’s a breakdown of the typical process:
1. Network Configuration:
- Network Connectivity: Ensuring that the computer is connected to the network is crucial. This typically involves a wired or wireless connection.
- Network Address: The "J drive" is associated with a specific network address (IP address) that identifies the storage server.
- Network Protocols: The network uses specific protocols like SMB (Server Message Block) or NFS (Network File System) to communicate and transfer data.
2. User Authentication:
- Domain Credentials: Users often need to provide valid domain credentials (username and password) to access the "J drive." These credentials are verified by the network server to authorize access.
- Permissions: Access rights are typically granted to users or groups, defining their level of interaction with the "J drive," including read-only, write, or administrative permissions.
Methods of Accessing the "J Drive":
- Network Drive Mapping: This method involves connecting the "J drive" to a specific drive letter on the user’s computer. This allows users to access the shared storage as if it were a local drive.
- File Explorer (Windows): Users can access the "J drive" through the File Explorer application. This typically involves navigating to the "Network" or "This PC" section and locating the shared drive.
- Network File System (NFS): This protocol is commonly used in Linux and macOS environments. Users can mount the "J drive" using the appropriate command-line tools or GUI utilities.
Troubleshooting Common Issues:
- Network Connectivity: Ensure a stable internet connection and check if the network server is online.
- Credentials: Verify the username and password used for authentication.
- Permissions: Confirm that the user has sufficient permissions to access the "J drive."
- Network Drive Mapping: If the "J drive" is not mapped correctly, remap the drive using the appropriate network settings.
- Network Protocols: Ensure that the network protocols used for communication are properly configured.
FAQs:
Q: What if the "J drive" is not visible on my computer?
A: This could be due to several factors, including network connectivity issues, incorrect credentials, missing permissions, or a misconfigured network drive mapping.
Q: How do I map the "J drive" to my computer?
A: The process for mapping a network drive varies depending on the operating system. Consult your system’s documentation or online resources for specific instructions.
Q: What if I forget my password for the "J drive"?
A: Contact your network administrator or IT support for assistance with password recovery.
Q: Can I access the "J drive" from a remote location?
A: Yes, accessing the "J drive" remotely is possible if the network server allows it and appropriate security measures are in place.
Tips for Accessing the "J Drive:
- Verify Network Connectivity: Ensure a stable internet connection and confirm the network server is online.
- Double-Check Credentials: Use the correct username and password for authentication.
- Review Permissions: Check if you have the necessary permissions to access the "J drive."
- Contact IT Support: If you encounter persistent issues, contact your IT support for assistance.
Conclusion:
The "J drive" represents a shared storage location within a network environment, offering numerous advantages for data management, collaboration, and security. Accessing the "J drive" typically involves network configuration, user authentication, and appropriate permissions. By understanding the process and troubleshooting common issues, users can effectively utilize this valuable resource.


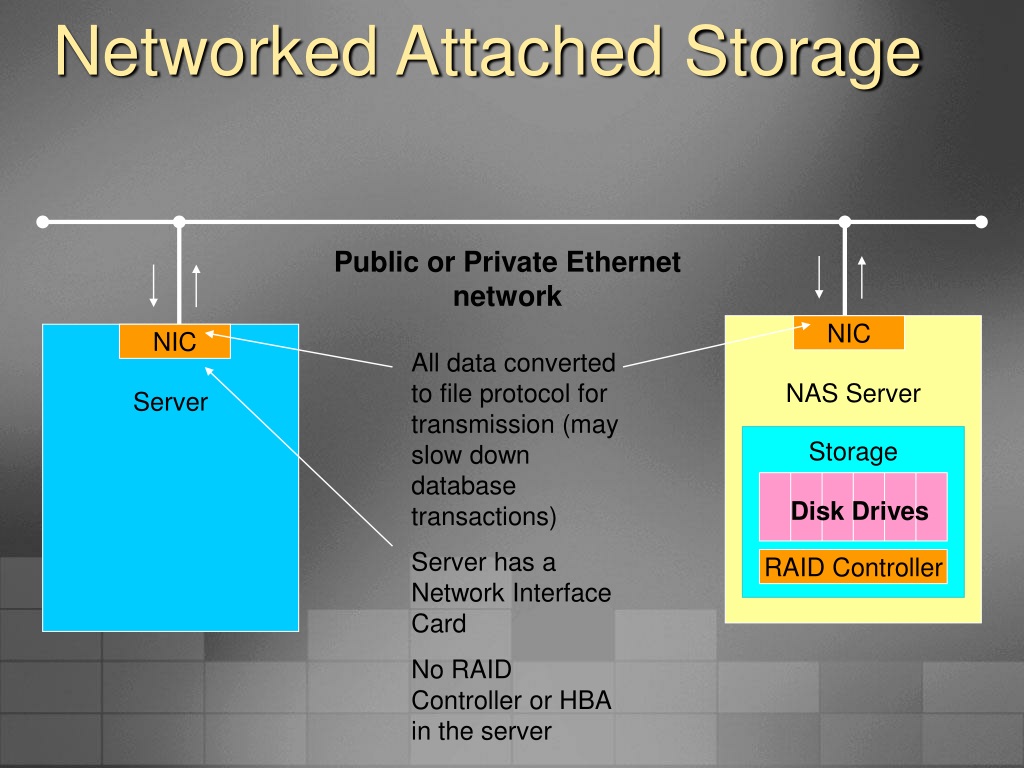


Closure
Thus, we hope this article has provided valuable insights into Understanding Networked Storage: The Role of Drive Letters. We appreciate your attention to our article. See you in our next article!