The Evolution of Windows Defender: A Comprehensive Look at Microsoft’s Integrated Security Solution
Related Articles: The Evolution of Windows Defender: A Comprehensive Look at Microsoft’s Integrated Security Solution
Introduction
With enthusiasm, let’s navigate through the intriguing topic related to The Evolution of Windows Defender: A Comprehensive Look at Microsoft’s Integrated Security Solution. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
The Evolution of Windows Defender: A Comprehensive Look at Microsoft’s Integrated Security Solution

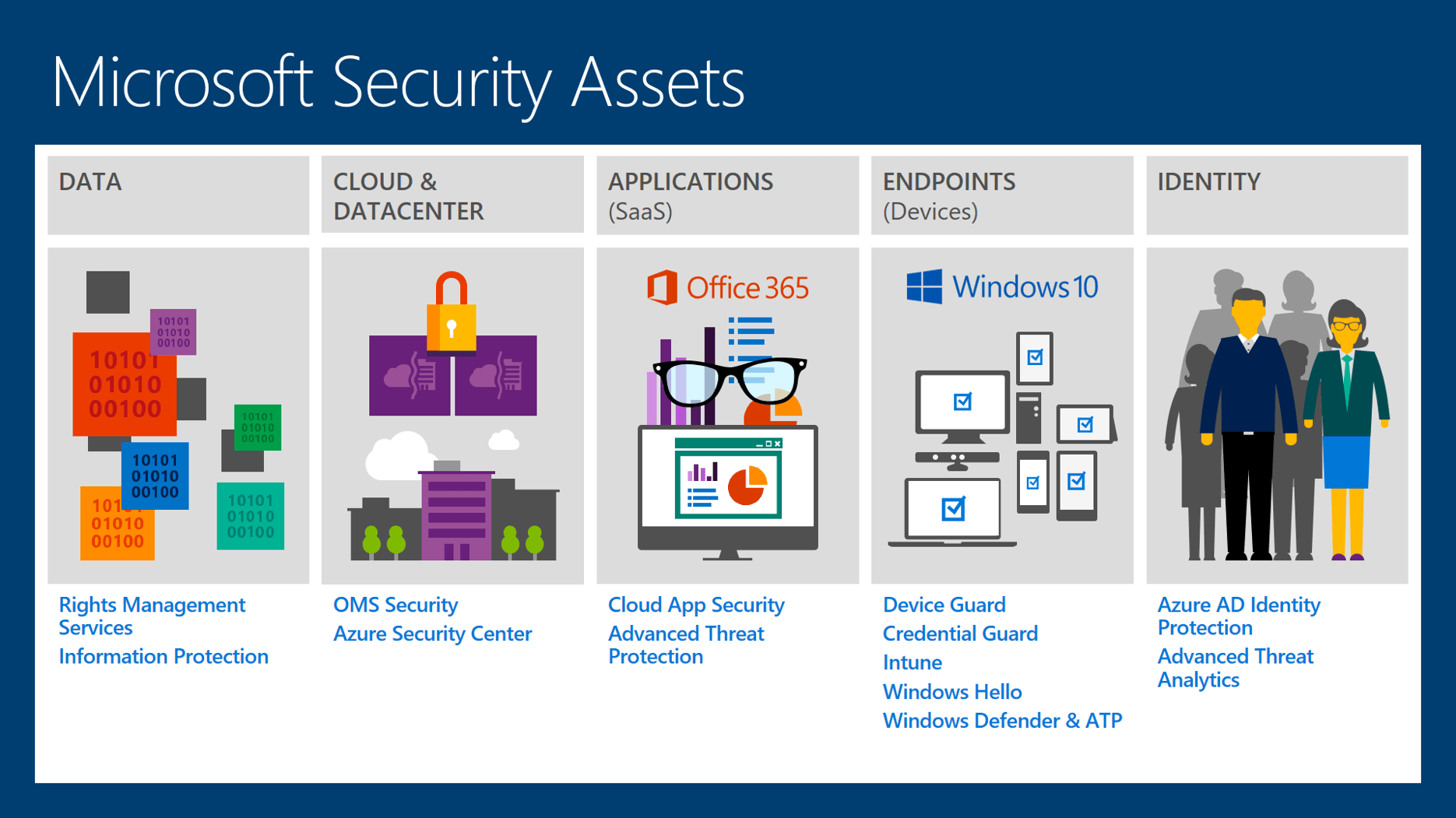
Windows Defender, the built-in antivirus solution integrated within Windows operating systems, has undergone a significant transformation over the years. Initially perceived as a basic security tool, it has evolved into a robust and comprehensive security suite capable of protecting against a wide range of threats. This article explores the strengths and limitations of Windows Defender, examining its effectiveness in the current cybersecurity landscape.
The Foundation: From "AntiSpyware" to Comprehensive Security
Windows Defender’s origins can be traced back to 2005 with the release of "Windows Defender Beta," designed primarily to combat spyware and other intrusive software. Over the years, its capabilities expanded significantly, becoming "Microsoft Security Essentials" in 2009 and finally integrating directly into Windows 8 as "Windows Defender." This integration signified a strategic shift towards a holistic approach to security, encompassing not only antivirus but also anti-malware, firewall, and other protective measures.
Core Strengths: A Multi-layered Approach to Protection
Windows Defender’s effectiveness stems from its multi-layered approach to security. Its key strengths include:
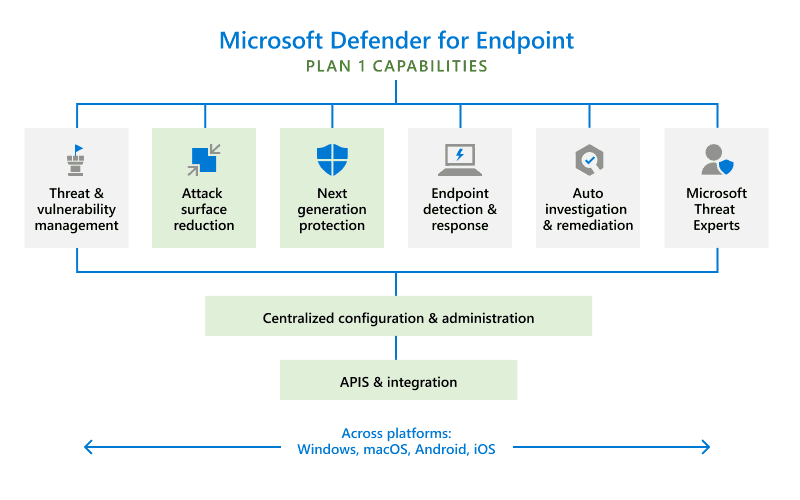
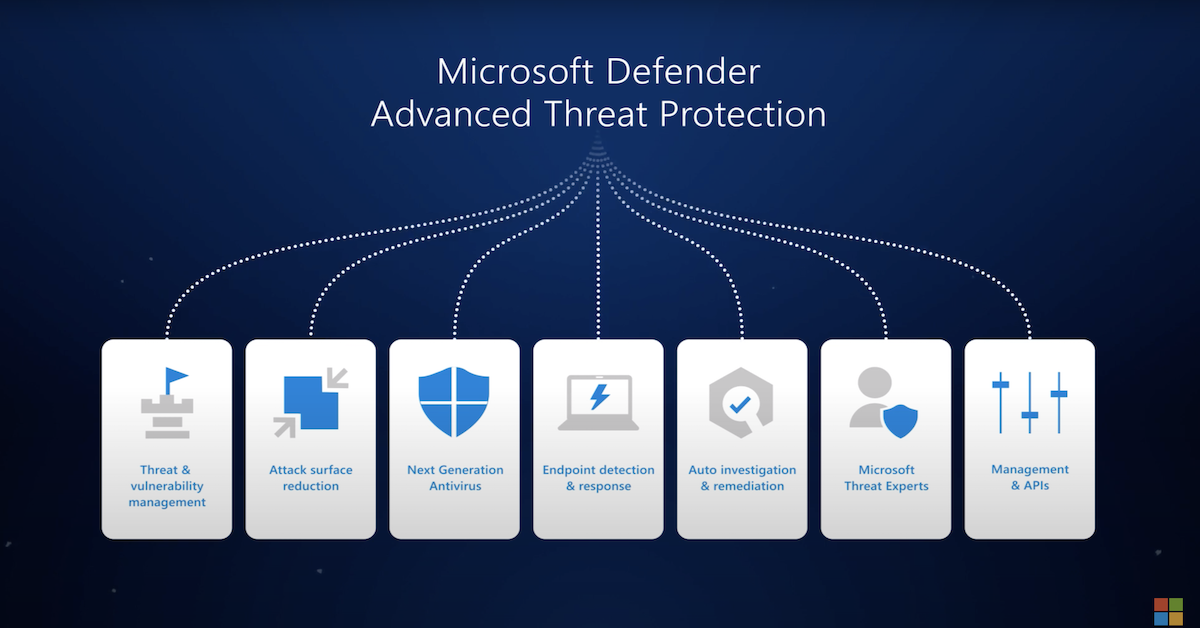
- Real-time Protection: Windows Defender constantly monitors the system for suspicious activity, scanning files, applications, and websites in real-time. This proactive approach helps to prevent infections before they can cause harm.
- Cloud-Based Protection: Utilizing Microsoft’s cloud infrastructure, Windows Defender leverages machine learning and threat intelligence to identify and block emerging threats, even those previously unknown. This cloud-based approach enhances its ability to adapt to the ever-evolving threat landscape.
- Exploit Protection: Windows Defender’s exploit protection feature safeguards against vulnerabilities in software applications, preventing attackers from exploiting weaknesses to gain unauthorized access to the system.
- Firewall Management: Windows Defender Firewall acts as a barrier between the computer and the internet, controlling incoming and outgoing network traffic. This feature helps to prevent unauthorized access and data breaches.
- Anti-Phishing: Windows Defender helps to identify and block phishing websites, which attempt to steal sensitive information such as passwords and credit card details.
- Automatic Updates: Windows Defender automatically updates its definition files and security mechanisms, ensuring that it remains current with the latest threats and vulnerabilities.
Beyond the Basics: Additional Features for Enhanced Security
Windows Defender offers several additional features that enhance its overall security posture:
- Windows Security App: This centralized interface provides a comprehensive overview of the system’s security status, allowing users to manage various security settings, view scan results, and access other security-related tools.
- Controlled Folder Access: This feature protects sensitive folders from unauthorized modifications, preventing ransomware and other malicious software from compromising important data.
- App & Browser Control: Users can configure specific settings for application and browser behavior, limiting the execution of potentially risky programs and restricting access to potentially harmful websites.
- Network Security: Windows Defender monitors network traffic for suspicious activity, alerting users to potential threats and providing tools to manage network connectivity.
- Performance Optimization: Windows Defender’s efficient resource management ensures minimal impact on system performance, allowing users to enjoy a smooth and uninterrupted computing experience.
Addressing Limitations: Considerations for Optimal Security
While Windows Defender offers a robust set of security features, it’s crucial to acknowledge its limitations:
- Limited Customization: While Windows Defender offers some customization options, its settings are not as granular as those found in dedicated third-party antivirus solutions. This limitation may hinder advanced users who require fine-grained control over security settings.
- Potential for False Positives: Like any antivirus solution, Windows Defender can occasionally flag legitimate files or applications as threats, leading to false positives. This can disrupt workflows and require manual intervention to resolve.
- Limited Proactive Threat Detection: While Windows Defender leverages cloud-based intelligence, it may not be as proactive in identifying and blocking zero-day threats, which are unknown and undetected by traditional antivirus methods.
- Limited Protection Against Targeted Attacks: Windows Defender may struggle to protect against highly targeted attacks, particularly those leveraging sophisticated malware or exploiting specific vulnerabilities.
Balancing the Scales: A Comprehensive Perspective
It’s important to approach the evaluation of Windows Defender from a comprehensive perspective. While it may not be the ultimate solution for all security needs, it provides a robust baseline of protection for most users.
- For the Average User: Windows Defender offers more than sufficient protection against common threats, providing a reliable and user-friendly security solution.
- For Businesses and Advanced Users: While Windows Defender can be a good starting point, organizations and individuals with heightened security requirements may benefit from supplementing it with additional security measures, such as dedicated endpoint protection solutions or threat intelligence services.
FAQs: Addressing Common Questions
Q: Is Windows Defender good enough?
A: For the average user, Windows Defender provides more than adequate protection against common threats. Its real-time protection, cloud-based intelligence, and integrated security features make it a reliable and effective solution.
Q: Is Windows Defender better than other antivirus software?
A: This is a complex question with no definitive answer. While Windows Defender offers strong protection, dedicated third-party antivirus solutions often provide more advanced features, customization options, and specialized threat detection capabilities. The best choice depends on individual needs and security requirements.
Q: Can I use Windows Defender along with other antivirus software?
A: It is not recommended to run multiple antivirus solutions simultaneously, as this can lead to conflicts and performance issues. Windows Defender is designed to work seamlessly with the Windows operating system and should be sufficient for most users.
Q: Does Windows Defender slow down my computer?
A: Windows Defender is designed to be efficient and have minimal impact on system performance. However, resource usage can vary depending on factors such as system specifications and the level of activity on the computer.
Q: How do I check if Windows Defender is working?
A: To access the Windows Security app, search for "Windows Security" in the Start menu. This app provides a comprehensive overview of your system’s security status, including real-time protection, firewall settings, and virus and threat protection scan results.
Tips for Optimizing Windows Defender
- Keep Windows Defender Up-to-Date: Ensure that Windows Defender’s definition files and security mechanisms are regularly updated to stay current with the latest threats.
- Enable Controlled Folder Access: Configure Controlled Folder Access to protect sensitive folders from unauthorized modifications, mitigating the risk of ransomware attacks.
- Review Scan Results: Regularly review scan results to identify and address any potential security issues.
- Use Strong Passwords: Employ strong passwords for all accounts, including your Windows user account, to prevent unauthorized access.
- Be Cautious with Attachments and Links: Avoid opening email attachments or clicking on links from unknown sources, as these can be vectors for malware infections.
- Keep Software Up-to-Date: Regularly update all software applications to patch vulnerabilities that could be exploited by attackers.
- Practice Safe Browsing Habits: Be mindful of the websites you visit and avoid clicking on suspicious links or downloading files from untrusted sources.
Conclusion: A Powerful and Evolving Security Solution
Windows Defender has evolved from a basic antispyware tool into a comprehensive security solution capable of protecting against a wide range of threats. Its real-time protection, cloud-based intelligence, and integrated security features make it a reliable and effective choice for most users. While it may not be the ultimate solution for all security needs, it provides a strong foundation for protecting against common threats. By staying informed about its features, limitations, and best practices for optimization, users can leverage Windows Defender to enhance their overall security posture and safeguard their digital lives.



Closure
Thus, we hope this article has provided valuable insights into The Evolution of Windows Defender: A Comprehensive Look at Microsoft’s Integrated Security Solution. We thank you for taking the time to read this article. See you in our next article!
