Navigating the Windows User Account Control Landscape: A Comprehensive Guide
Related Articles: Navigating the Windows User Account Control Landscape: A Comprehensive Guide
Introduction
With great pleasure, we will explore the intriguing topic related to Navigating the Windows User Account Control Landscape: A Comprehensive Guide. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
Navigating the Windows User Account Control Landscape: A Comprehensive Guide
User Account Control (UAC) is a security feature integrated into modern Windows operating systems, designed to protect users from malicious software and unauthorized changes to the system. It acts as a gatekeeper, prompting users for confirmation before any program attempts to make significant alterations to the system, including installing software, modifying system settings, or accessing protected areas. This security measure is crucial in safeguarding the integrity and stability of the Windows environment.
Understanding the Core of User Account Control
The foundation of UAC lies in the principle of "least privilege." This principle dictates that users should only have access to the resources they need to perform their tasks, minimizing the potential for accidental or malicious damage. UAC implements this by separating user accounts into two levels:
- Standard Users: These accounts have limited privileges, preventing them from installing software, changing system settings, or accessing protected areas without administrator approval.
- Administrators: These accounts have full control over the system, allowing them to perform any action, including installing software, modifying system settings, and accessing protected areas.
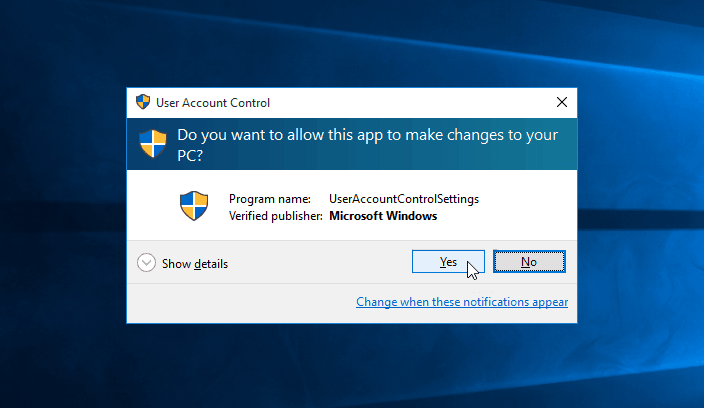
When a program attempts to perform an action that requires elevated privileges, UAC intervenes. A prompt appears, informing the user about the action and requesting their approval. This prompt serves as a critical checkpoint, allowing users to make informed decisions about granting access to the program.
Benefits of User Account Control: A Shield Against Threats
The implementation of UAC offers a multitude of benefits, significantly enhancing the security of the Windows operating system:
- Reduced Vulnerability to Malicious Software: UAC acts as a significant barrier against malware, preventing it from making unauthorized changes to the system. By requiring user approval for elevated actions, UAC hinders malware from silently installing itself, spreading to other systems, or modifying critical system files.
- Protection Against Unauthorized Changes: UAC prevents unauthorized users or malicious programs from making changes to critical system settings, ensuring the stability and security of the operating system. This safeguard protects against accidental or intentional modifications that could compromise the system’s functionality or expose it to vulnerabilities.
- Enhanced System Integrity: By limiting the actions that users can perform without administrator approval, UAC maintains the integrity of the system, preventing accidental or malicious modifications that could lead to system instability or data loss.
- Increased Awareness of System Actions: UAC prompts users to confirm actions requiring elevated privileges, raising awareness of the potential impact of these actions. This increased awareness helps users make informed decisions about granting access to programs and promotes a more secure computing environment.
Navigating User Account Control: A Guide to Common Interactions
UAC prompts appear in various forms, each indicating a specific action requiring user approval. Understanding these prompts is crucial for navigating UAC effectively:
- Elevated Prompt: This prompt appears when a program needs to access protected areas of the system, such as installing software, making changes to system settings, or accessing specific files. This prompt requires the user to provide their administrator password to proceed.
- Standard User Prompt: This prompt appears when a program needs to perform an action that requires administrator privileges but does not require access to protected areas. This prompt allows the user to grant or deny access to the program without providing their administrator password.
- User Account Control Setting Adjustment: This prompt appears when a user attempts to modify UAC settings, allowing them to adjust the level of security and control they desire.
Addressing Common User Account Control Concerns
While UAC offers significant security benefits, users often encounter challenges or have questions regarding its operation. Addressing these concerns is crucial for a smooth and secure user experience:
1. UAC Prompts are Frequent and Annoying:
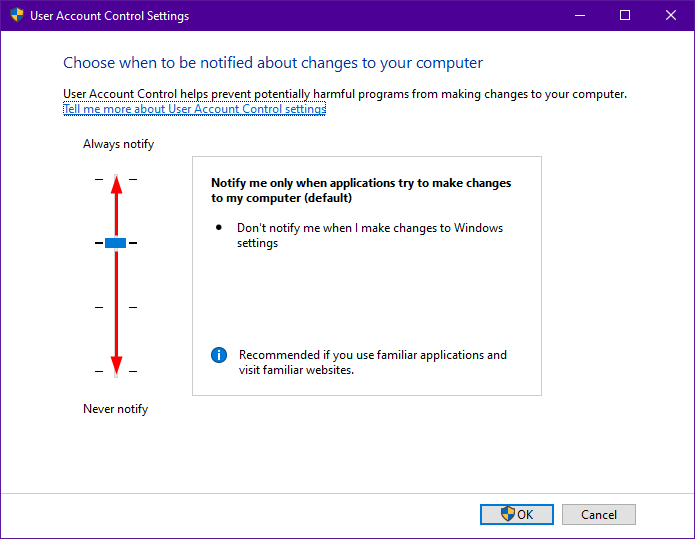
- Solution: Users can adjust UAC settings to reduce the frequency of prompts. The "Never Notify" setting disables all prompts, but it is highly discouraged due to the significant security risks it poses. A more balanced approach involves setting the UAC prompt level to "Notify me only when apps try to make changes to my computer." This setting ensures that only critical actions trigger prompts, reducing the frequency while maintaining a reasonable level of security.
2. UAC Prompts Require Administrator Password:
- Solution: While UAC prompts requiring administrator passwords might seem inconvenient, they are essential for maintaining system security. To avoid frequent password entries, users can create a dedicated administrator account for tasks requiring elevated privileges. This practice allows them to use their regular user account for everyday tasks, minimizing the need for frequent password entries.
3. UAC Prevents Access to Certain Programs:
- Solution: UAC can sometimes block access to legitimate programs due to its strict security measures. In such cases, users can temporarily disable UAC to grant access to the program. However, it is crucial to understand the risks associated with disabling UAC and to re-enable it once the program has been accessed.
4. UAC Settings are Confusing:
- Solution: Understanding UAC settings can be challenging. Users can consult online resources or contact Microsoft support for assistance in configuring UAC settings to their specific needs and preferences.
5. UAC Interferes with System Performance:
- Solution: While UAC adds a slight overhead to system performance, it is generally negligible. If users experience significant performance issues, they can adjust UAC settings to reduce the frequency of prompts, minimizing the impact on system performance.
FAQs Regarding User Account Control
Q: Can I permanently disable User Account Control?
A: While disabling UAC is possible, it is strongly discouraged due to the significant security risks it poses. Disabling UAC leaves the system vulnerable to malicious software and unauthorized changes, potentially compromising the system’s integrity and stability.
Q: Why does User Account Control require my administrator password?
A: UAC requires administrator passwords for actions that could potentially harm the system. This measure prevents unauthorized users or malicious software from making changes to the system without the knowledge and consent of the administrator.
Q: How can I adjust User Account Control settings?
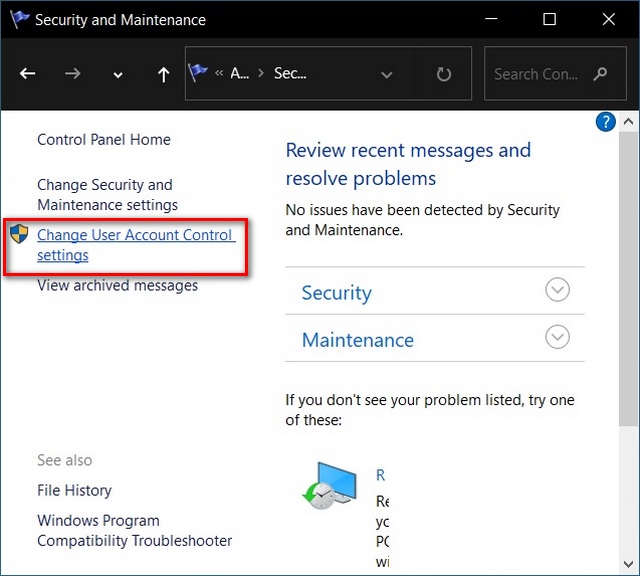
A: To adjust UAC settings, users can follow these steps:
- Open the Control Panel.
- Navigate to "User Accounts and Family Safety."
- Select "User Accounts."
- Click on "Change User Account Control settings."
- Adjust the slider to choose the desired level of UAC security.
Q: What are the different levels of User Account Control?
A: UAC offers four levels of security:
- Never Notify: Disables all UAC prompts, significantly increasing security risks.
- Always Notify: Notifies users for all actions requiring elevated privileges, potentially leading to frequent prompts.
- Notify me only when apps try to make changes to my computer: Notifies users only for critical actions, providing a balanced approach to security.
- Use the default settings: Sets UAC to its default level of security, providing a moderate level of protection.
Tips for Effective User Account Control Management
- Regularly Review UAC Settings: Regularly review UAC settings to ensure they are aligned with the user’s security needs and preferences.
- Use Separate Administrator Accounts: Create a dedicated administrator account for tasks requiring elevated privileges, minimizing the need for frequent password entries on regular user accounts.
- Keep Software Up-to-Date: Ensure that all software, including the operating system, is up-to-date to mitigate potential vulnerabilities exploited by malicious software.
- Be Cautious with Program Installations: Exercise caution when installing programs from unknown sources, as they may contain malicious software.
Conclusion: Embracing the Power of User Account Control
User Account Control is a vital security feature in modern Windows operating systems, safeguarding users from malicious software and unauthorized changes. By understanding its principles, benefits, and common concerns, users can effectively manage UAC settings to enhance their system’s security and stability. While UAC might initially seem inconvenient, its importance in protecting against threats and maintaining system integrity cannot be overstated. By embracing the power of UAC, users can create a more secure and reliable computing environment.

![[How To] Configure User Account Control Settings In Windows 10/8/7](https://htse.kapilarya.com/How-To-Configure-User-Account-Control-Settings-In-Windows-10-1.png)



Closure
Thus, we hope this article has provided valuable insights into Navigating the Windows User Account Control Landscape: A Comprehensive Guide. We hope you find this article informative and beneficial. See you in our next article!