Circumventing Windows 10 Login Security: A Comprehensive Guide
Related Articles: Circumventing Windows 10 Login Security: A Comprehensive Guide
Introduction
With great pleasure, we will explore the intriguing topic related to Circumventing Windows 10 Login Security: A Comprehensive Guide. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
Circumventing Windows 10 Login Security: A Comprehensive Guide
This document provides a comprehensive overview of methods used to bypass Windows 10 login security, emphasizing the importance of understanding the ethical and legal implications associated with these techniques. It is crucial to acknowledge that bypassing login security is generally considered unethical and potentially illegal, particularly if done without the owner’s consent. This information should be used for educational purposes only and should not be applied in any manner that violates the law or infringes on the privacy of others.
Understanding Windows 10 Login Security
Windows 10 employs robust security measures to protect user accounts and sensitive data. The login process involves verifying the user’s identity through a password, PIN, or biometric authentication, such as fingerprint scanning. This security layer prevents unauthorized access to the system and its contents.
Circumventing Login Security: A Multifaceted Approach
Bypassing Windows 10 login security can be achieved through various methods, each with its own level of complexity and potential consequences. These methods can broadly be categorized into:
1. Password Recovery and Reset:
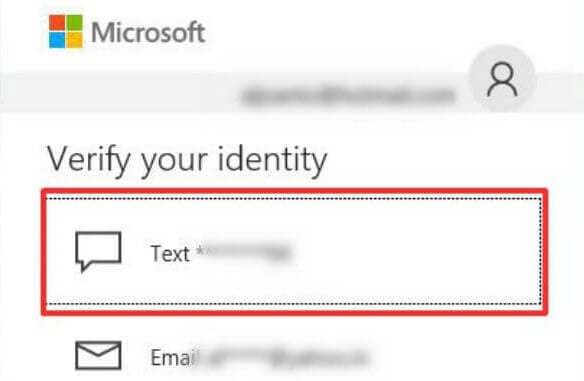
- Microsoft Account Recovery: If the user has forgotten their password, they can utilize Microsoft’s password recovery system. This involves providing personal information linked to the account, such as email address, phone number, or security questions.
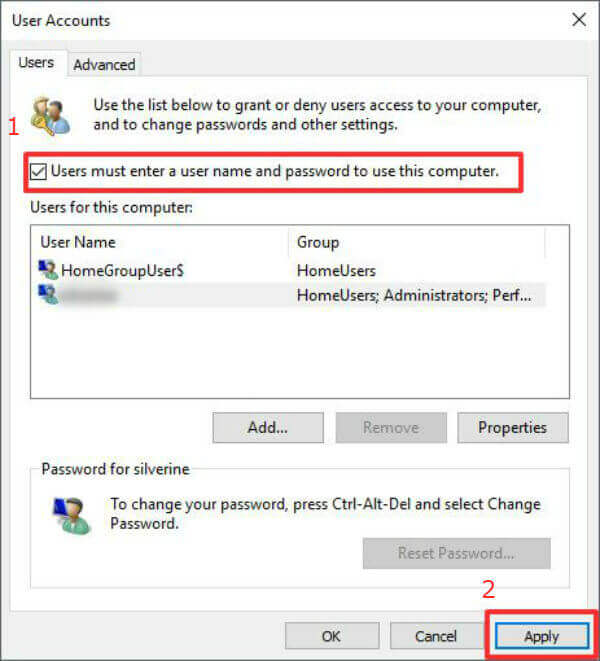
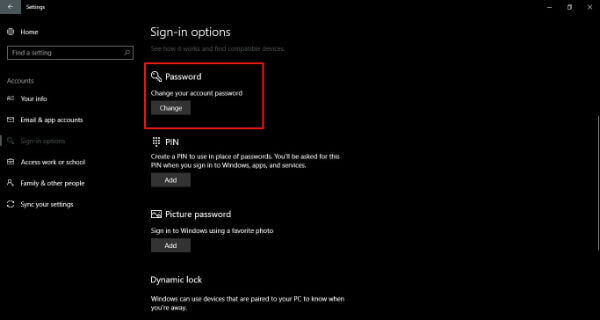
- Local Account Password Reset: For accounts created locally on the device, Windows provides built-in password reset options. This often requires a system administrator’s password or a USB recovery drive created beforehand.
2. Utilizing System Tools:
- Command Prompt (CMD): The command prompt can be used to manipulate system settings and potentially access user accounts. However, this requires advanced knowledge of system commands and can be risky if not performed correctly.
- Boot Options: Accessing the advanced boot options allows users to choose different startup modes. This includes safe mode, which can disable certain security features and provide access to system files.
3. External Tools and Software:
- Password Cracking Software: These tools attempt to guess passwords by using brute force or dictionary attacks. However, their effectiveness depends on the complexity of the password and the available computing resources.
- Password Reset Disks: Creating a password reset disk before losing the password can provide a means to reset the login credentials.
4. Exploiting System Vulnerabilities:
- System Security Flaws: Exploiting vulnerabilities in the operating system or its applications can potentially bypass login security measures. However, this is a highly specialized and risky approach, often requiring advanced technical skills.
5. Physical Access and Manipulation:
- Boot from External Media: Booting from a USB drive or CD containing a live operating system can bypass the Windows login process. This allows access to the system’s files and potentially modify login settings.
- Hardware Manipulation: Removing or modifying certain hardware components, such as the hard drive, can potentially circumvent login security. However, this approach is highly invasive and can damage the system.
Ethical and Legal Considerations
Circumventing Windows 10 login security raises ethical and legal concerns. It is crucial to understand the following:
- Unauthorized Access: Bypassing login security without the owner’s consent is considered unauthorized access and may violate privacy laws.
- Data Theft: Accessing someone else’s account can lead to data theft, including personal information, financial data, and confidential documents.
- Criminal Activity: Using these methods for malicious purposes, such as hacking or identity theft, can result in serious legal consequences.
Importance of Responsible Use
The methods described in this document are provided for educational purposes only. It is crucial to use them responsibly and ethically. It is strongly discouraged to use these techniques for any purpose that violates the law or infringes on the privacy of others.
FAQs: Addressing Common Questions
Q: Is it legal to bypass Windows 10 login security?
A: Bypassing login security without the owner’s consent is generally illegal and considered a violation of privacy.
Q: What are the risks associated with bypassing login security?
A: The risks include unauthorized access, data theft, and legal consequences.
Q: Can I use these methods to access my own account if I forget my password?
A: Yes, some methods, such as password recovery options or creating a password reset disk, can be used to access your own account if you forget your password.
Q: Is it possible to bypass Windows 10 login security without any knowledge?
A: Bypassing login security often requires technical knowledge and can be challenging.
Q: What are the best practices for protecting my Windows 10 account?
A: Best practices include using strong passwords, enabling two-factor authentication, and keeping your system updated with the latest security patches.
Tips for Secure Login Practices
- Use Strong Passwords: Choose complex passwords that combine uppercase and lowercase letters, numbers, and symbols.
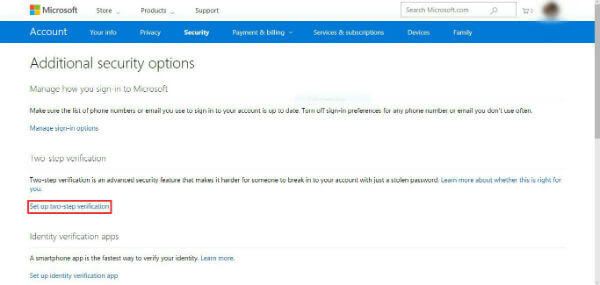
- Enable Two-Factor Authentication: This adds an extra layer of security by requiring a second verification step, such as a code sent to your phone.
- Keep Your System Updated: Regularly install the latest security updates to patch vulnerabilities.
- Be Cautious of Suspicious Links and Emails: Avoid clicking on links or opening attachments from unknown senders.
- Use Antivirus Software: Install and keep your antivirus software up to date to protect against malware.
Conclusion
Circumventing Windows 10 login security is a complex and multifaceted issue. While various methods exist, it is crucial to understand the ethical and legal implications associated with these techniques. This information should be used for educational purposes only and should not be applied in any manner that violates the law or infringes on the privacy of others. Responsible use and strong security practices are essential for protecting your data and ensuring the integrity of your Windows 10 system.


Closure
Thus, we hope this article has provided valuable insights into Circumventing Windows 10 Login Security: A Comprehensive Guide. We hope you find this article informative and beneficial. See you in our next article!