Bypassing Windows Network Setup: A Comprehensive Guide to Advanced Network Configuration
Related Articles: Bypassing Windows Network Setup: A Comprehensive Guide to Advanced Network Configuration
Introduction
In this auspicious occasion, we are delighted to delve into the intriguing topic related to Bypassing Windows Network Setup: A Comprehensive Guide to Advanced Network Configuration. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
Bypassing Windows Network Setup: A Comprehensive Guide to Advanced Network Configuration

The Windows network setup process, while designed to be user-friendly, can sometimes hinder advanced network configurations or be inconvenient in specific scenarios. In such instances, bypassing the default setup can provide greater control and flexibility, enabling users to tailor their network environment to specific requirements. This article explores various methods to bypass Windows network setup, outlining their functionalities, advantages, and potential drawbacks.
Understanding the Need to Bypass Network Setup
The standard Windows network setup process typically involves automatic IP address assignment, network discovery, and file sharing. While this approach simplifies network management for most users, it can become restrictive in certain situations, such as:
- Static IP Address Configuration: When precise IP addresses are required for specific devices or services, automatic assignment can lead to conflicts or hinder compatibility.
- Network Security: Bypassing network setup allows for granular control over firewall settings, network sharing options, and other security parameters, enhancing network isolation and data protection.
- Advanced Network Environments: Complex network topologies, such as those utilizing VLANs, VPNs, or custom DNS configurations, may require manual intervention beyond the standard setup.
- Troubleshooting Network Issues: Bypassing network setup can be crucial for diagnosing and resolving network problems, as it provides direct access to network configuration settings.
Methods to Bypass Windows Network Setup
Several methods can be employed to bypass the standard Windows network setup process. Each method offers distinct advantages and disadvantages, making it essential to choose the most appropriate approach based on the specific network configuration goals.
1. Manual Network Configuration
The most direct way to bypass the automated network setup is through manual configuration. This involves directly setting network parameters like IP address, subnet mask, default gateway, and DNS server addresses.
Steps:
- Open Network and Sharing Center: Access the Network and Sharing Center through the Control Panel.
- Change Adapter Settings: Click on "Change adapter settings" in the left-hand menu.
- Properties: Right-click the network adapter you wish to configure and select "Properties."
- Internet Protocol Version 4 (TCP/IPv4): Select "Internet Protocol Version 4 (TCP/IPv4)" and click "Properties."
- Manual Configuration: Choose the "Use the following IP address" option and enter the required IP address, subnet mask, default gateway, and preferred DNS server address.
Advantages:
- Complete Control: Provides full control over network settings, enabling customization beyond the standard setup.
- Troubleshooting: Facilitates troubleshooting network issues by allowing direct modification of network parameters.
Disadvantages:
- Technical Expertise: Requires a good understanding of network configuration and IP addressing.
- Error Potential: Incorrect configuration can lead to network connectivity problems.
2. Command Prompt Configuration
The Command Prompt (CMD) provides a powerful interface for managing network settings. Using commands like "ipconfig," "netsh," and "route," users can configure IP addresses, network adapters, and routing tables directly.
Steps:
- Open Command Prompt: Search for "cmd" in the Windows search bar and open the Command Prompt as administrator.
- IP Address Configuration: Use the "ipconfig /release" and "ipconfig /renew" commands to release and renew the IP address, respectively.
- Static IP Address Assignment: Use the "ipconfig /set ipaddress" command to assign a static IP address.
- Subnet Mask and Default Gateway: Utilize the "ipconfig /set subnetmask" and "ipconfig /set gateway" commands to configure the subnet mask and default gateway.
Advantages:
- Flexibility: Offers a flexible and versatile approach to network configuration.
- Scripting: Allows for scripting and automation of network configuration tasks.
Disadvantages:
- Advanced Knowledge: Requires a deeper understanding of network commands and syntax.
- Error Prone: Incorrect commands can disrupt network connectivity.
3. Network Configuration Using PowerShell
PowerShell provides a more advanced and object-oriented scripting environment for managing network settings. Using PowerShell cmdlets, users can automate complex network configurations and manage network devices remotely.
Steps:
- Open PowerShell: Search for "powershell" in the Windows search bar and open PowerShell as administrator.
- Network Adapter Management: Use cmdlets like "Get-NetAdapter" and "Set-NetAdapter" to manage network adapters.
- IP Address Configuration: Use cmdlets like "Get-NetIPAddress" and "Set-NetIPAddress" to configure IP addresses, subnet masks, and default gateways.
- DNS Configuration: Utilize cmdlets like "Get-DnsClientServerAddress" and "Set-DnsClientServerAddress" to manage DNS settings.
Advantages:
- Automation: Enables scripting and automation of network configuration tasks.
- Remote Management: Allows for remote management of network settings.
- Advanced Functionality: Provides access to a wide range of network management features.
Disadvantages:
- Steep Learning Curve: Requires a significant understanding of PowerShell scripting.
- Complexity: May be overwhelming for users without prior PowerShell experience.
4. Using Third-Party Tools
Various third-party network configuration tools offer user-friendly interfaces for managing network settings without requiring deep technical knowledge. These tools often provide intuitive visual representations of network configurations and simplify complex tasks.
Advantages:
- Ease of Use: Simplifies network configuration through graphical interfaces.
- Feature-Rich: Offers a wide range of features, including network monitoring and troubleshooting tools.
Disadvantages:
- Cost: Some third-party tools may require a paid subscription.
- Compatibility: Ensure compatibility with the specific operating system and network environment.
Importance and Benefits of Bypassing Network Setup
Bypassing Windows network setup offers significant advantages for users seeking greater control and flexibility over their network environment. These benefits include:
- Precise Network Configuration: Enables the implementation of specific IP addresses, network security settings, and advanced network configurations.
- Troubleshooting and Diagnostics: Facilitates the identification and resolution of network connectivity issues.
- Network Optimization: Allows for the fine-tuning of network settings to optimize performance and efficiency.
- Enhanced Security: Provides granular control over firewall rules, network sharing options, and other security parameters.
Frequently Asked Questions (FAQs)
Q: Is it safe to bypass Windows network setup?
A: Bypassing network setup is generally safe when performed correctly and with a proper understanding of network configuration principles. However, incorrect configuration can lead to network connectivity issues or security vulnerabilities.
Q: What are the risks of bypassing network setup?
A: The primary risks include:
- Network Connectivity Issues: Incorrect configuration can result in network connectivity problems.
- Security Vulnerabilities: Improperly configured network settings can expose devices to security threats.
- Data Loss: Incorrect network configuration can potentially lead to data loss.
Q: Can I revert to the standard network setup after bypassing it?
A: Yes, you can revert to the standard network setup by resetting network settings or reinstalling the operating system.
Q: What are some best practices for bypassing network setup?
A:
- Thorough Research: Understand the network configuration principles and best practices before making any changes.
- Backup Data: Backup important data before making any network configuration changes.
- Test Thoroughly: Test network connectivity and functionality after making any changes.
- Use Reliable Sources: Refer to reputable sources for network configuration instructions.
Conclusion
Bypassing Windows network setup offers a powerful mechanism for users seeking advanced network configurations and greater control over their network environment. While it requires a deeper understanding of network principles and configuration techniques, it empowers users to tailor their network to specific requirements, enhance network security, and optimize network performance. By carefully considering the methods and best practices outlined in this article, users can leverage the benefits of bypassing network setup while minimizing potential risks.
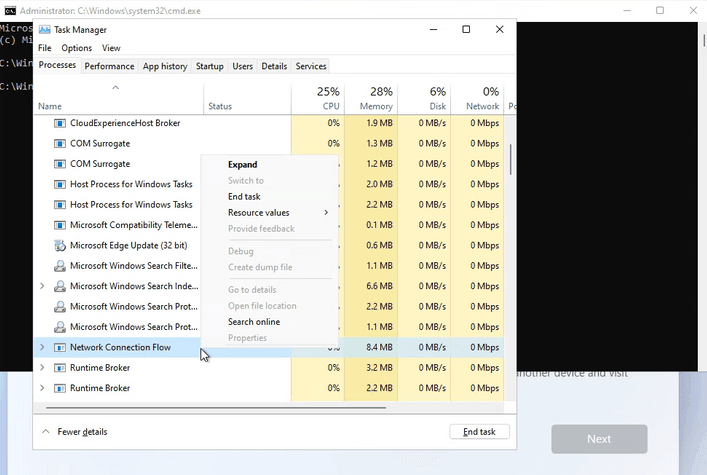
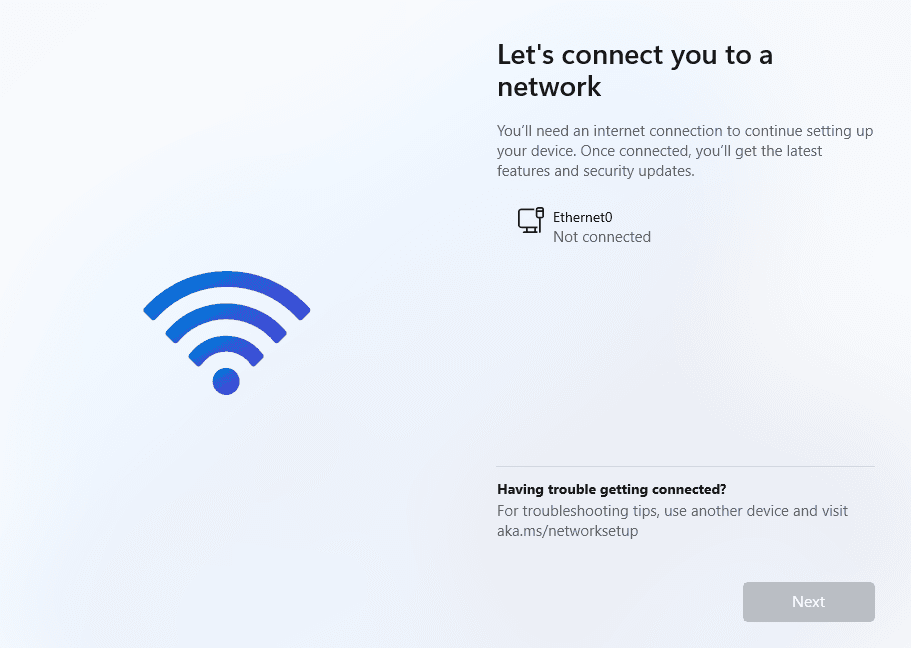

:max_bytes(150000):strip_icc()/AdvancedNetworkSettings-3587fd9d84854349a985815b2c40dec0.jpg)

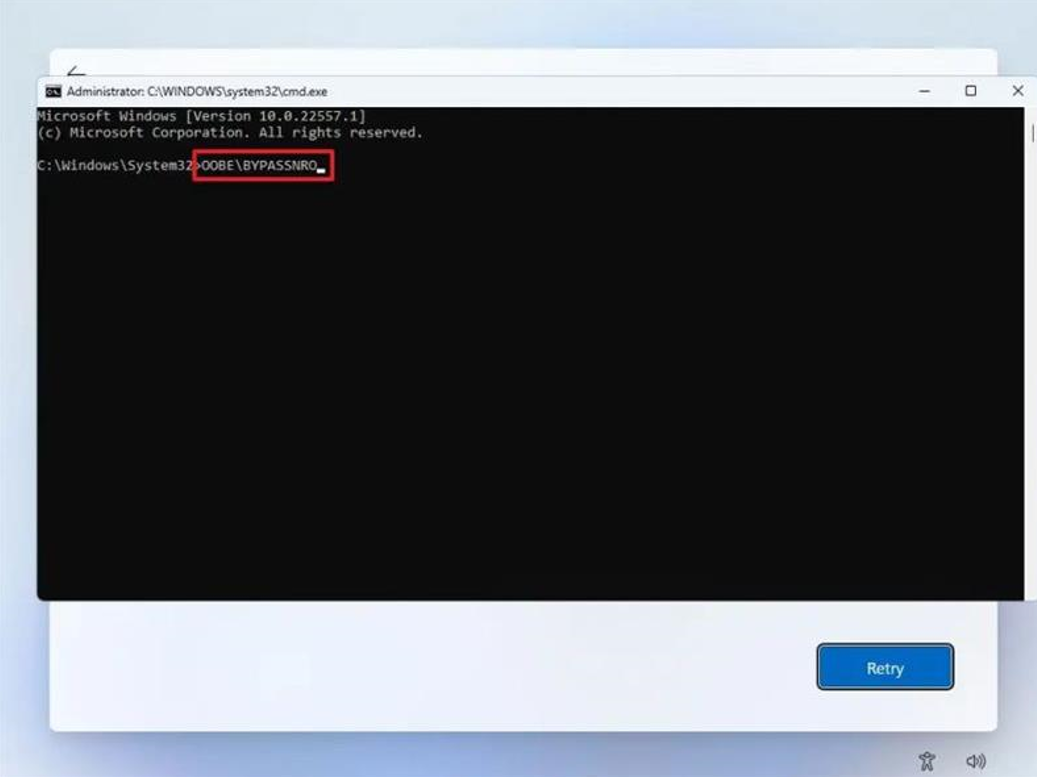
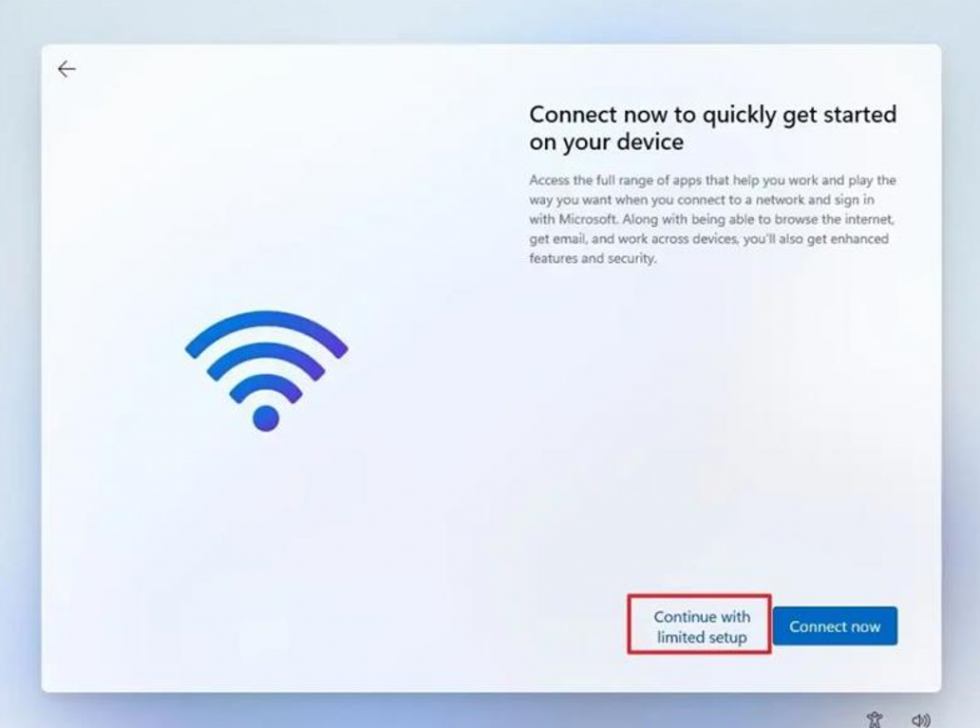
:max_bytes(150000):strip_icc()/NetworkReset-65bc046f024a45d4b0aa435e41968167.jpg)
Closure
Thus, we hope this article has provided valuable insights into Bypassing Windows Network Setup: A Comprehensive Guide to Advanced Network Configuration. We hope you find this article informative and beneficial. See you in our next article!